SSH is a protocol that allows the exchange of data between two computers over an untrusted network securely. It ensures the privacy and integrity of the exchanged data and files over the untrusted network. This protocol runs in every server by default and in most computers.
The SSH protocol is also referred to as Secure Shell and allows the system Admins to remotely and securely log in to other servers and computers. This way, the SysAdmins are able to carry out their roles as if they were physically logged into the physical server.
The client machine requires strong authentication to remotely and securely log in to the server. The communication between the client and the server after successful login is enhanced through strong encryption to ensure data integrity and security. SSH is the preferred method as compared to non-protected login protocols e.g Telnet and insecure File Transfer Methods e.g FTP.
How SSH Server works
SSH server works on the client/server model. SSH client initiates the setup of a secure connection. The SSH server listens to the incoming clients’ secure connection requests on port 22 on the host machine and responds. The server then authenticates itself to the client by providing its public key. The SSH client verifies the public key and if it is successful, the SSH server provides the client access to the host system via user account permissions at the target host machine.
SSH key pairs are two encrypted secure keys used to authenticate a client to an SSH server. Each key pair consists of a public key and a private key. The client retains the private key which should be kept secret and encrypted at all times. If this key fell into the hands of hackers, they will access your server. The public key can be shared without any fear. It is uploaded to the server that the client wants to remotely connect through SSH.
Once the connection is made, the SysAdmin can now remotely do system administration, execute commands remotely on the CLI, transfer files between client and server, and secure the traffic of other applications.
The diagram below shows a simple illustration of the explanation of how the SSH server works.
Configure SSH Server on Rocky Linux 9 / AlmaLinux 9
We will cover the installation, configurations, and usage of SSH Server and client on Rocky Linux 9 / AlmaLinux 9.
1. Refresh your packages
To refresh your packages:
sudo dnf clean all2. Install openSSH Clients
To install the OpenSSH client on your Rocky Linux client machine, run the command below.
sudo dnf update -y
sudo dnf install openssh-clientsThe will most possibly be installed in your system as it comes defaulted in Rocky Linux repository of packages.
3. Install openSSH Server
Installing the OpenSSH server is equally an easy process. Execute this command:
sudo dnf install openssh-serverThe package should as well be installed by default in your system.
To start the service after installation:
sudo systemctl start sshdTo enable the service to start on the next boot:
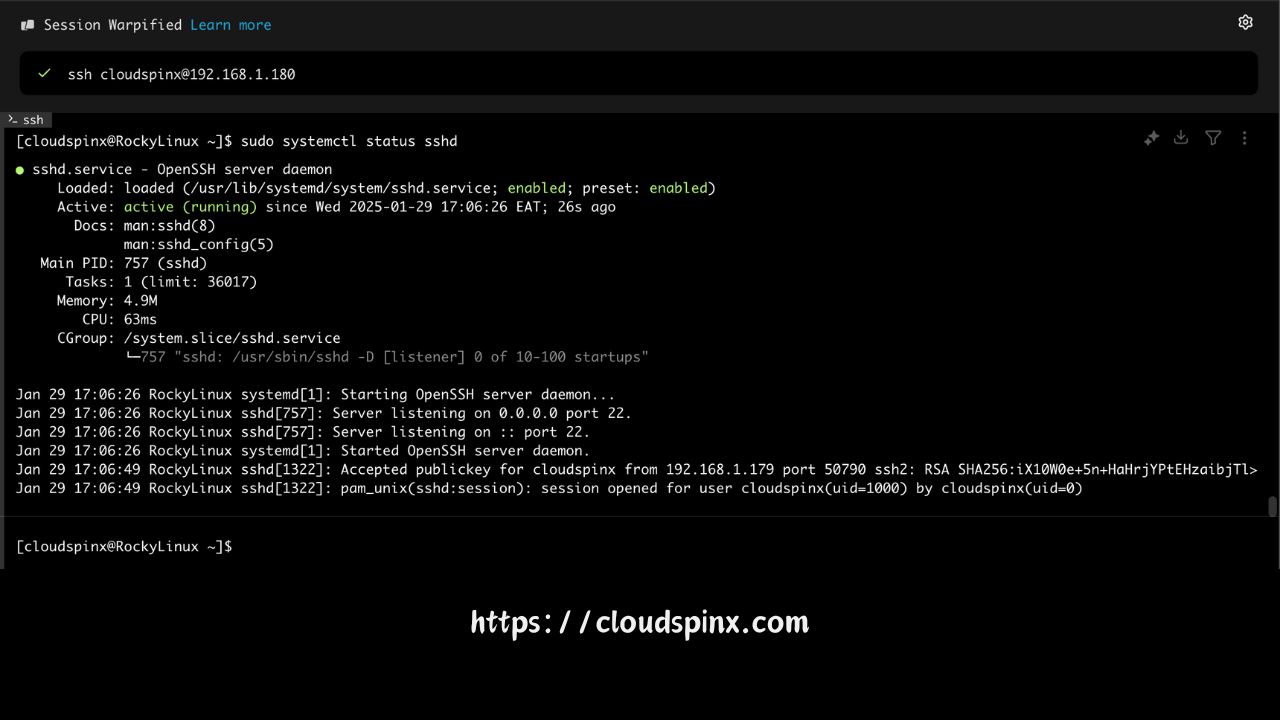
sudo systemctl enable sshdChecking status of installation:
● sshd.service - OpenSSH server daemon
Loaded: loaded (/usr/lib/systemd/system/sshd.service; enabled; preset: enabled)
Active: active (running) since Wed 2025-01-29 17:06:26 EAT; 26s ago
Docs: man:sshd(8)
man:sshd_config(5)
Main PID: 757 (sshd)
Tasks: 1 (limit: 36017)
Memory: 4.9M
CPU: 63ms
CGroup: /system.slice/sshd.service
└─757 "sshd: /usr/sbin/sshd -D [listener] 0 of 10-100 startups"
Jan 29 17:06:26 RockyLinux systemd[1]: Starting OpenSSH server daemon...
Jan 29 17:06:26 RockyLinux sshd[757]: Server listening on 0.0.0.0 port 22.
Jan 29 17:06:26 RockyLinux sshd[757]: Server listening on :: port 22.
Jan 29 17:06:26 RockyLinux systemd[1]: Started OpenSSH server daemon.
Jan 29 17:06:49 RockyLinux sshd[1322]: Accepted publickey for cloudspinx from 192.168.1.179 port 50790 ssh2: RSA SHA256:iX10W0e+5n+HaHrjYPtEHzaibjTl>
Jan 29 17:06:49 RockyLinux sshd[1322]: pam_unix(sshd:session): session opened for user cloudspinx(uid=1000) by cloudspinx(uid=0)
4. Configure Firewalld
To Configure the firewall to allow SSH connection through port 22, do the following.
1 ) Check if openSSH is currently registered with firewalld by running the command:
sudo firewall-cmd --list-allThe sample output :
public (active)
target: default
icmp-block-inversion: no
interfaces: enp1s0
sources:
services: cockpit dhcpv6-client http https ssh
ports:
protocols:
forward: no
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:To enable the OpenSSH application profile, run the command:
sudo firewall-cmd --add-service=ssh --permanent
sudo firewall-cmd --reloadIf your SSH daemon is configured to listen through a different port number, say 2222, allow this port by running the command:
sudo firewall-cmd --add-port=2222/tcp --permanent
sudo firewall-cmd --reload5. Changing ssh port (with selinux labeling), firewalld port open
You may wish to change the default ssh port 22 to something else. This is possible by editing the ssh configuration file. This configuration file is located at /etc/ssh/sshd_config. Simply use the text editor of your choice, scroll down to the port area, uncomment the line and insert the new port number.
sudo vim /etc/ssh/sshd_configThe output:
# If you want to change the port on a SELinux system, you have to tell
# SELinux about this change.
# semanage port -a -t ssh_port_t -p tcp #PORTNUMBER
#
#Port 22 ## Uncomment this line and insert your new port number ##
#AddressFamily any
#ListenAddress 0.0.0.0
#ListenAddress ::For example, modify the port number to 2222, to have an output as this:
# If you want to change the port on a SELinux system, you have to tell
# SELinux about this change.
# semanage port -a -t ssh_port_t -p tcp #PORTNUMBER
#
Port 2222
#AddressFamily any
#ListenAddress 0.0.0.0
#ListenAddress ::Save and quit your editor after making your changes.
The next step is to configure SELinux to allow port 2222 for SSH. Achieve this by executing the command:
The syntax:
semanage port -a -t ssh_port_t -p tcp #PORTNUMBERAllowing port 2222 using the syntax above:
sudo semanage port -a -t ssh_port_t -p tcp 2222Then allow the traffic through port 2222 through the firewall if it is running.
sudo firewall-cmd --add-port=2222/tcp --permanent
sudo firewall-cmd --reloadRestart the sshd service for the change to take effect:
sudo systemctl restart sshd You can confirm if the server is running on port 2222
sudo systemctl status sshdThe output:
● sshd.service - OpenSSH server daemon
Loaded: loaded (/usr/lib/systemd/system/sshd.service; enabled; vendor preset: enabled)
Active: active (running) since Wed 2025-01-29 10:37:34 EAT; 1min 18s ago
Docs: man:sshd(8)
man:sshd_config(5)
Main PID: 96758 (sshd)
Tasks: 1 (limit: 48737)
Memory: 1.1M
CGroup: /system.slice/sshd.service
└─96758 /usr/sbin/sshd -D [email protected],[email protected],aes256-ctr,aes256-cbc,[email protected],aes1>
Jan 29 10:37:34 RockLlinux systemd[1]: Starting OpenSSH server daemon...
Jan 29 10:37:34 RockyLinux sshd[96758]: Server listening on 0.0.0.0 port 2222.
Jan 29 10:37:34 RockyLinux sshd[96758]: Server listening on :: port 2222.
Jan 29 10:37:34 RockyLinux systemd[1]: Started OpenSSH server daemon.Very well, you have successfully managed to configure a different port number for OpenSSH Server.
6. How to ssh to remote systems
This can be done both on standard and non-standard ports. We will briefly examine the two in this section.
How to SSH to remote systems on non-standard ports.
To establish a connection to your server, all you need to do is open your terminal from the client-side and issue this command:
$ ssh your_username@host_ip_address
#OR
$ ssh <YOUR_FULLY_QUALIFIED_DOMAIN_NAME>From my client machine:
ssh [email protected]On issuing the above command, I get this output:
ssh: connect to host 192.168.1.180 port 22: Connection refusedThis is because I am trying to access my OpenSSH server on port number 22, and in our case in step 5 above, we changed the port from the default 22 to 2222.
How do we ssh to this server? This is a very simple process and is solved as follows:
$ ssh -p <YOUR_NEW_PORT> your_username@host_ip_addressAs shown below:
$ ssh -p 2222 [email protected]Once you press Enter, you will be prompted to enter the user password.
As shown below:
$ ssh -p 2222 [email protected]
[email protected]'s password:
Web console: https://RockyLinux:9090/ or https://192.168.1.180:9090/
Last login: Wed Jan 29 09:13:28 2021 from 192.168.1.179
[cloudspinx@RockyLinux ~]$ That was easy.
How to SSH to remote systems on standard ports
To SSH to remote systems on standard ports, simply run the command:
ssh your_username@host_ip_address As below:
ssh [email protected]I edited the configuration file /etc/ssh/sshd_config and allowed back the default standard port 22 to connect uisng the standard port.
7. Generating SSH Keys (On Workstation mostly)
To generate SSH keys, we use the command ssh-keygen followed by the type of the key to be generated.
ssh-keygen -t The option -t specifies the type of the key to be created. Several algorithms exist which include: rsa, dsa,ecdsa, and ed25519. The default algorithm type is RSA.
Let’s create an RSA key with a length of 2048 bits. Run the command:
ssh-keygen -b 2048 -t rsaThis command prompts you to Enter a file in which to save the key and default it to something like this (/home/Jil/.ssh/id_rsa). Accept the default path by pressing Enter or supplying your file to save the key.
Next, you are prompted to Enter a passphrase. Press Enter for none. However, it is recommended that you Enter the passphrase to protect your private key against unauthorized use.
Confirm your passphrase and press Enter.
The output:
$ ssh-keygen -b 2048 -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/home/cloudspinx/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/cloudspinx/.ssh/id_rsa.
Your public key has been saved in /home/cloudspinx/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:0d8nf6NIn1iNSzLyRLgEalH0t67CEOD51DSMNT cloudspinx@RockyLinux ## Edited for Security ##
The key's randomart image is:
+---[RSA 2048]----+
| Eo.O= |
| o. *.+o. |
| .. o.+.o... |
| o oo...o... |
| oo. So o. o .|
| .o . + o+ |
| o o * + oo|
| o * O + o|
| .. + = |
+----[SHA256]-----+
The output reveals that a public key and a private key have been created and saved in /home/Jil/.ssh/id_rsa. The public key has .pub appended to it to specify that it is a public key.
8. Using SSH keys
In the previous step, we created the Public and Private keys using the RSA algorithm. In this section, we will look at how to use the generated SSH keys.
Option 1 : The long route:
This method is the longer one but it’s good to learn it too.
1 ) Copy the public key generated in our previous step to a clipboard:
cat /home/cloudspinx/.ssh/id_rsa.pub2 ) Connect to a remote server via ssh. For the sake of this article, I will connect to the Fedora server which runs on 192.168.1.182
ssh [email protected] Once logged in to your remote server, set the server to accept connection through a public key. To do this we will create a .ssh directory if it doesn’t already exist.
3 ) Create a .ssh directory.
mkdir .ssh4 ) Change to this directory:
cd .ssh5 ) Using a text editor, create a file called authorized_keys and paste your public key here.
$ vim authorized_keys
#Paste-public-keySave and quit from the editor and disconnect from the remote server.
6 ) Now SSH to remote server again.
ssh [email protected]You will notice that no password will be required to log in.
As shown below:
[cloudspinx@RockyLinux ~]$ ssh [email protected]
Web console: https://Fedora-client:9090/ or https://192.168.1.182:9090/
Last login: Mon Dec 6 15:55:36 2021 from 192.168.1.180
[cloudspinx@Fedora-client ~]$ The reason no password was required is that we added the public key on the authorized file.
If you wish to see more information on the connection, you use the -v option as shown below.
ssh -v [email protected]That explains the long way to do it.
Option 2 : The short way
To use Public key authentication, we must copy the public key to the server and install it in an authorized_keys file. This is done using a tool called ssh-copy-id which follows this syntax.
ssh-copy-id -i ~/.ssh/id_rsa.pub cloudspinx@remote_hostTo use this tool, you must specify the remote host to connect to and the user account associated with that remote host. This is the account where this public key will be copied to as shown below:
ssh-copy-id -i ~/.ssh/id_rsa.pub [email protected]This gives this output:
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/home/cloudspinx/.ssh/id_rsa.pub"
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
[email protected]'s password:
Number of key(s) added: 1
Now try logging into the machine, with: "ssh '[email protected]'"
and check to make sure that only the key(s) you wanted were added.Notice that one key was added to our remote server i.e 192.168.201.3
Now try to login into your remote server and you will notice that no password is required.
$ ssh [email protected]
Web console: https://Fedora-client:9090/ or https://192.168.1.182:9090/
Last login: Wed Jan 29 16:26:05 2021 from 192.168.1.180
[cloudspinx@Fedora-client ~]$ Cool right? why use the long route if you can use a shorter one?
9. ssh-agent and ssh-add commands
ssh-agent command handles the passwords for SSH private keys. This command caches the key into the memory to avoid having to key in your paraphrase key every time you log in. ssh-add command prompts the user for a private key password and adds it to the list maintained by ssh-agent. When a user adds a password to the ssh-agent, he will be prompted to key it in whenever he tries to ssh or to copy over ssh i.e SCP.
As described above, the public key must be copied to the remote server in the ~/.ssh/authorized_keys file.
To use ssh-agent and ssh-add commands, do the following:
1 ) On your agent machine run the command to start the ssh-agent: i.e
$ eval `ssh-agent`
#or
$ eval "$(ssh-agent)"Output:
Agent pid 107736To confirm the ssh-agent is running:
$ ps aux | grep ssh-agentThe output:
$ ps aux | grep ssh-agent
Jil 107736 0.0 0.0 27436 520 ? Ss 17:20 0:00 ssh-agent
Jil 107810 0.0 0.0 12136 1036 pts/0 S+ 17:23 0:00 grep --color=auto ssh-agent2 ) Next run the command ssh-add to add a private key to the ssh-agent
ssh-add ~/.ssh/id_rsaThe command executes to the identity path of the private key: It might prompt you for the paraphrase password.
output:
Identity added: /home/cloudspinx/.ssh/id_rsa (cloudspinx@RockyLinux)If you now ssh your remote server again, it will require no password;
$ ssh [email protected]
Web console: https://Fedora-client:9090/ or https://192.168.1.182:9090/
Last login: Wed Jan 29 16:58:56 2021 from 192.168.1.1803 ) Logout and enter the command below:
kill $SSH_AGENT_PIDAs shown below:
kill 107736This command kills the ssh session.
10. Copy files over ssh with scp
SCP is a command-line utility that allows you to securely copy files and directories between two machines. With SCP you can copy files and directories between a local system to a remote system, between a remote system to a local machine, or between multiple remote systems to a local system.
The syntax is as below:
$ scp [OPTION] [user@]SRC_HOST:]file1 [user@]DEST_HOST:]file2The available [OPTION]: cipher, ssh configuration, ssh port, limit, recursive copy, etc.
The SRC_HOST:]file1 is the source file.
The DEST_HOST:]file2 is the destination file
SCP options can be found on man scp with the most used ones being:
- -P Specifies the port to connect to on the remote host.
- -p Preserves modification times, access times, and modes from the original file.
- -q Quiet mode – This suppresses the progress meter and non-error messages.
- -r Recursively copy entire directories.
- -v Verbose mode
- -T Disable strict filename checking
We will look at an example to illustrate this.
On my local machine, I have a pdf document Training_Certificate.pdf that I wish to copy to my ~ on my Fedora server. This is how am to use the SCP command to achieve this.
scp -v Training_Certificate.pdf [email protected]:~I have employed the -v option to see how the process proceeds.
Sample output:
Executing: program /usr/bin/ssh host 192.168.1.182, user cloudspinx, command scp -v -t ~
OpenSSH_8.0p1, OpenSSL 1.1.1k FIPS 25 Mar 2021
debug1: Reading configuration data /home/cloudspinx/.ssh/config
debug1: Reading configuration data /etc/ssh/ssh_config
debug1: Reading configuration data /etc/ssh/ssh_config.d/05-redhat.conf
debug1: Reading configuration data /etc/crypto-policies/back-ends/openssh.config
debug1: configuration requests final Match pass
debug1: re-parsing configuration
.
.
.
debug1: Sending env LC_CTYPE = en_US.UTF-8
debug1: Sending env XMODIFIERS = @im=ibus
debug1: Sending command: scp -v -t ~
Sending file modes: C0664 214181 Training_Certificate.pdf
Sink: C0664 214181 Training_Certificate.pdf
Training_Certificate.pdf 100% 209KB 153.4KB/s 00:01
debug1: client_input_channel_req: channel 0 rtype exit-status reply 0
debug1: channel 0: free: client-session, nchannels 1
Transferred: sent 216540, received 2532 bytes, in 2.3 seconds
Bytes per second: sent 92630.3, received 1083.1
debug1: Exit status 0To confirm if the file was successfully transferred, I will log in to my Fedora server and see if I can see the file in my home directory.
ssh [email protected]Then check on my home directory:
[email protected]'s password:
Web console: https://Fedora-client:9090/ or https://192.168.1.182:9090/
Last login: Wed Jan 29 17:30:59 2021 from 192.168.201.2
[cloudspinx@Fedora-client ~]$ cd /home/cloudspinx/
[cloudspinx@Fedora-client ~]$ ls -l
total 220
-rwxr-xr-x. 1 cloudspinx cloudspinx 5006 Sep 29 23:18 3FfADm1
-rw-rw-r--. 1 cloudspinx cloudspinx 214181 Jan 29 18:00 Training_Certificate.pdfThe file was securely copied to my remote server from my local machine.
I will now securely copy a file named newfile.txt which resides on my Fedora server to my local machine running on Rocky Linux. This time I will recursively copy this file.
To securely copy this file, we use the remote location as a source and the local location as the destination. It is good to note that this is not executed on the remote location but on the local location.
As shown below:
scp -r [email protected]:~cloudspinx/newfile.txt ~/Desktop/newfile.txtLet’s see if our file newfile.txt has been copied to the local location (Rocky Linux System) on the Desktop.
09:42:57 cloudspinx@RockyLinux ~ → cd Desktop/
/home/cloudspinx/Desktop
09:43:09 cloudspinx@RockyLinux Desktop → ls -l
total 304
-rw-rw-r--. 1 cloudspinx cloudspinx 17479 Oct 9 19:34 'DCUK 10.10.2021 FUND RAISER.ods'
-rw-rw-r--. 1 cloudspinx cloudspinx 17496 Oct 9 19:35 'DCUK 10.10.2021 FUND RAISER.ots'
-rw-rw-r--. 1 cloudspinx cloudspinx 8294 Oct 15 15:10 'DCUK 10.10.2021 FUND RAISER.xlsx'
-rw-r--r--. 1 cloudspinx cloudspinx 13 Dec 7 09:42 newfile.txt
-rw-------. 1 cloudspinx cloudspinx 252048 Dec 3 15:16 'resignation letter page 2.pdf'We have successfully and securely copied our file from the remote location to the local location.
Conclusion
That sums up our article on how to Install and Configure SSH Server on Rocky Linux 9 / AlmaLinux 9. I hope it was insightful and that you have acquired much more knowledge. There is still much more to learn and more resources can be found on official ssh documentation or man pages. Thank you so much for taking the time to read this.
If you wish to see more guides, the following articles will assist you.