OSSEC (Open-Source HIDS SECurity ) is a free and open-source Hosted-Based Intrusion Detection System (HIDS). OSSEC plays a critical role in monitoring and giving information on what is running or happening to a server at a particular time. Performs the following functions;
- analysing logs
- integrity checking and monitoring
- keeping track of windows registry
- rootkit detection.
- Real-time alerting and active responses
Software is capable of monitoring and providing intrusion reports across all operating systems; Linux, FreeBSD, OpenBSD, OS X, Solaris, Windows and many more.
OSSEC has an agent that is capable of collecting logs of the events in the server for analysis. On a server that is running an OSSEC server by default, an agent is installed to monitor local activities. If you need to monitor a remote server using a local OSSEC server then you will need to install an OSSEC agent on the remote server then connect it OSSEC server. In this article, am going to take you through how you can install an OSSEC agent in Ubuntu. Let’s check on the features of OSSEC before we proceeded to the installation part.
Features of OSSEC
- Open-Source – Is a free software that can be acquire at zero cost.
- Universal – OSSEC is used/runs on almost all Operating Systems.
- Active response. – Gives a real-time response on attack or changes in the system.
- Log Based Intrusion Detection (LIDs) – Detects attack on server usng logs.
- Compliance Auditing – Complies with common standards such as CIS benchmarking and PCI-DSS.
- File Integrity Monitoring (FIM) – Mantains a forensic copy of data as it changes over time.
- Capable of detecting Rootkit and Malware in the system.
- Is termed as a system inventory as it collects system infomation for both hardware and software.
Step 1: Update your Ubuntu System
Before doing any installation ensure that your system is up to date.
sudo apt update -y
sudo apt upgrade -y Step 2: Setup OSSEC Server
For our agent to work, it will need a server where it will be sending reports and alerts. This step is only for someone who doesn’t have OSSEC Server installed. If you have an OSSEC server then go to Step 3.
Step 2.1: Install Setup dependencies
Run this command to install the required components for the application.
sudo apt install build-essential gcc make unzip sendmail inotify-tools expect libevent-dev libpcre2-dev libz-dev libssl-dev libsystemd-dev -y Step 2.2: Download Latest OSSEC HIDS
Visit GitHub to find the latest version of OSSEC.
cd
VERSION=$(curl -s https://api.github.com/repos/ossec/ossec-hids/releases/latest | grep tag_name | cut -d '"' -f 4)
wget https://github.com/ossec/ossec-hids/archive/$VERSION.tar.gzStep 2.3: Install OSSEC HIDS on Ubuntu
Extract the file downloaded:
tar xvf $VERSION.tar.gzNavigate to ossec unzipped folder then run the installation script.
cd ossec-hids-${VERSION}
sudo sh install.shSelect your preferred language.
(en/br/cn/de/el/es/fr/hu/it/jp/nl/pl/ru/sr/tr) [en]: enOn the next screen, press ENTER to continue.
OSSEC HIDS v3.8.0 Installation Script - http://www.ossec.net
You are about to start the installation process of the OSSEC HIDS.
You must have a C compiler pre-installed in your system.
- System: Linux ubuntu-noble 6.8.0-53-generic
- User: root
- Host: ubuntu-noble
-- Press ENTER to continue or Ctrl-C to abort. --On kind of installation select server.
1- What kind of installation do you want (server, agent, local, hybrid or help)? server
- Server installation chosen. serverSetting up the installation environment.
- Choose where to install the OSSEC HIDS [/var/ossec]: <Press ENTER>
- Installation will be made at /var/ossec .
Configuring the OSSEC HIDS.
3.1- Do you want e-mail notification? (y/n) [y]: y
- What's your e-mail address? ossec@localhost
- We found your SMTP server as: 127.0.0.1
- Do you want to use it? (y/n) [y]: y
--- Using SMTP server: 127.0.0.1
3.2- Do you want to run the integrity check daemon? (y/n) [y]: y
- Running syscheck (integrity check daemon).
3.3- Do you want to run the rootkit detection engine? (y/n) [y]: y
- Running rootcheck (rootkit detection).
3.4- Active response allows you to execute a specific
command based on the events received. For example,
you can block an IP address or disable access for
a specific user.
More information at:
http://www.ossec.net/en/manual.html#active-response
- Do you want to enable active response? (y/n) [y]: n
- Active response disabled.
3.5- Do you want to enable remote syslog (port 514 udp)? (y/n) [y]: y
- Remote syslog enabled.
3.6- Setting the configuration to analyze the following logs:
-- /var/log/auth.log
-- /var/log/syslog
-- /var/log/dpkg.log
- If you want to monitor any other file, just change
the ossec.conf and add a new localfile entry.
Any questions about the configuration can be answered
by visiting us online at http://www.ossec.net .
--- Press ENTER to continue ---Give it some time to complete the installation.
- System is Debian (Ubuntu or derivative).
- Init script modified to start OSSEC HIDS during boot.
- Configuration finished properly.
- To start OSSEC HIDS:
/var/ossec/bin/ossec-control start
- To stop OSSEC HIDS:
/var/ossec/bin/ossec-control stop
- The configuration can be viewed or modified at /var/ossec/etc/ossec.conf
Thanks for using the OSSEC HIDS.
If you have any question, suggestion or if you find any bug,
contact us at https://github.com/ossec/ossec-hids or using
our public maillist at
https://groups.google.com/forum/#!forum/ossec-list
More information can be found at http://www.ossec.net
--- Press ENTER to finish (maybe more information below). ---
- In order to connect agent and server, you need to add each agent to the server.
Run the 'manage_agents' to add or remove them:
/var/ossec/bin/manage_agentsStep 3: Install OSSEC Agent on Ubuntu
Now that we have the OSSEC server up and running, let us set up the agent in a different server and add it to the OSSEC server.
Step 3.1: Download Latest Version.
At this point repeat Step 2.1 and Step 2.2 exactly the way they are.
Step 3.2: Install OSSEC HIDS Agent.
Navigate to OSSEC generated folder on unzipping and run the installation script.
cd ossec-hids-${VERSION}
sudo sh install.shSet your preferred language. In my case, am choosing English (en).
(en/br/cn/de/el/es/fr/hu/it/jp/nl/pl/ru/sr/tr) [en]: enOn the new screen, press <ENTER> to continue with the installation.
OSSEC HIDS v3.6.0 Installation Script - http://www.ossec.net
You are about to start the installation process of the OSSEC HIDS.
You must have a C compiler pre-installed in your system.
- System: Linux tinc 5.4.0-29-generic
- User: root
- Host: tinc
-- Press ENTER to continue or Ctrl-C to abort. --Select the type of installation as the agent.
1- What kind of installation do you want (server, agent, local, hybrid or help)? agentLeave installation environment to default.
2- Setting up the installation environment.
- Choose where to install the OSSEC HIDS [/var/ossec]: PRESS ENTER
- Installation will be made at /var/ossec .
Add OSSEC server to connect to
3- Configuring the OSSEC HIDS.
3.1- What's the IP Address or hostname of the OSSEC HIDS server?: 172.12.24.10
- Adding Server IP 172.12.24.10
Run integrity daemon.
3.2- Do you want to run the integrity check daemon? (y/n) [y]: y
- Running syscheck (integrity check daemon).
Enable rootkit detection engine.
3.3- Do you want to run the rootkit detection engine? (y/n) [y]: y
- Running rootcheck (rootkit detection).
Disable active responses.
3.4 - Do you want to enable active response? (y/n) [y]: n
- Active response disabled.
You will be lead to screen of this kind.
3.5- Setting the configuration to analyze the following logs:
-- /var/log/auth.log
-- /var/log/syslog
-- /var/log/dpkg.log
-- /var/log/nginx/access.log (apache log)
-- /var/log/nginx/error.log (apache log)
- If you want to monitor any other file, just change
the ossec.conf and add a new localfile entry.
Any questions about the configuration can be answered
by visiting us online at http://www.ossec.net .
--- Press ENTER to continue ---
Once the agent is successfully installed, the message below will pop up on your screen. Press ENTER finish.
- System is Debian (Ubuntu or derivative).
- Init script modified to start OSSEC HIDS during boot.
- Configuration finished properly.
- To start OSSEC HIDS:
/var/ossec/bin/ossec-control start
- To stop OSSEC HIDS:
/var/ossec/bin/ossec-control stop
- The configuration can be viewed or modified at /var/ossec/etc/ossec.conf
Thanks for using the OSSEC HIDS.
If you have any question, suggestion or if you find any bug,
contact us at https://github.com/ossec/ossec-hids or using
our public maillist at
https://groups.google.com/forum/#!forum/ossec-list
More information can be found at http://www.ossec.net
--- Press ENTER to finish (maybe more information below). ---Step 4: Add OSSEC Agent on OSSEC Server
Now that we have OSSEC Server and Agent running, we are going to add Agent to the server for it to be sending logs of events to server. Before you add the agent, make sure that you allow port 1514 in UDP protocol to allow communication between server and agent.
sudo ufw allow 1514/udp
sudo ufw reloadAdd the agent to the server by running this command on the server:
$ sudo /var/ossec/bin/manage_agents
****************************************
* OSSEC HIDS v3.6.0 Agent manager. *
* The following options are available: *
****************************************
(A)dd an agent (A).
(E)xtract key for an agent (E).
(L)ist already added agents (L).
(R)emove an agent (R).
(Q)uit.
Choose your action: A,E,L,R or Q: ASelect <A> to add an agent option from the above menu.
Provide the Name and IP address of the agent host.
Adding a new agent (use '\q' to return to the main menu).
Please provide the following:
* A name for the new agent: NEW
* The IP Address of the new agent: 172.12.24.12
* An ID for the new agent[001]:<ENTER>Summary of your agent.
Agent information:
ID:001
Name:NEW
IP Address:172.12.24.12
Confirm adding it?(y/n): Y
Agent added with ID 001.Extract key for an agent by selecting option E in the menu below.
****************************************
* OSSEC HIDS v3.6.0 Agent manager. *
* The following options are available: *
****************************************
(A)dd an agent (A).
(E)xtract key for an agent (E).
(L)ist already added agents (L).
(R)emove an agent (R).
(Q)uit.
Choose your action: A,E,L,R or Q: EOn the screen shown, provide the ID of the agent to extract the key for.
Available agents:
ID: 001, Name: NEW, IP: 172.12.24.12
Provide the ID of the agent to extract the key (or '\q' to quit): 001
Agent key information for '001' is:
MDA------------------------------------------------------------------------------------2Q5YjU1MQ==
** Press ENTER to return to the main menu.Exit the menu now.
****************************************
* OSSEC HIDS v3.6.0 Agent manager. *
* The following options are available: *
****************************************
(A)dd an agent (A).
(E)xtract key for an agent (E).
(L)ist already added agents (L).
(R)emove an agent (R).
(Q)uit.
Choose your action: A,E,L,R or Q: q
** You must restart OSSEC for your changes to take effect.
manage_agents: Exiting.
manage_agents: Exiting.Restart the OSSEC server to apply the changes:
$ sudo /var/ossec/bin/ossec-control restart
Killing ossec-monitord ..
Killing ossec-logcollector ..
Killing ossec-remoted ..
Killing ossec-syscheckd ..
Killing ossec-analysisd ..
Killing ossec-maild ..
ossec-execd not running ..
OSSEC HIDS v3.6.0 Stopped
Starting OSSEC HIDS v3.6.0...
Started ossec-maild...
Started ossec-execd...
Started ossec-analysisd...
Started ossec-logcollector...
Started ossec-remoted...
Started ossec-syscheckd...
Started ossec-monitord...
Completed.Add Key to OSSEC Agent
Run this command on Agent host to begin.
$ sudo /var/ossec/bin/manage_agents
****************************************
* OSSEC HIDS v3.6.0 Agent manager. *
* The following options are available: *
****************************************
(I)mport key from the server (I).
(Q)uit.
Choose your action: I or Q: IPaste the key you extracted from OSSEC server.
* Provide the Key generated by the server.
* The best approach is to cut and paste it.
*** OBS: Do not include spaces or new lines.
Paste it here (or '\q' to quit): MDAxIE==================================================================================5YjU1MQ==Confirm if the Key belongs to the listed Agent ID, name and IP.
Agent information:
ID:001
Name:NEW
IP Address:172.12.24.12
Confirm adding it?(y/n): y
2021/10/04 19:28:16 manage_agents: ERROR: Cannot unlink /queue/rids/sender: No such file or directory
Added.
** Press ENTER to return to the main menu.Exit the menu.
****************************************
* OSSEC HIDS v3.6.0 Agent manager. *
* The following options are available: *
****************************************
(I)mport key from the server (I).
(Q)uit.
Choose your action: I or Q: q
** You must restart OSSEC for your changes to take effect.
manage_agents: Exiting.
manage_agents: Exiting.
Restart OSSEC services on the agent:
$ sudo /var/ossec/bin/ossec-control start
Killing ossec-logcollector ..
Killing ossec-syscheckd ..
Killing ossec-agentd ..
ossec-execd not running ..
OSSEC HIDS v3.6.0 Stopped
Starting OSSEC HIDS v3.6.0...
Started ossec-execd...
2021/10/06 21:45:19 ossec-agentd: INFO: Using notify time: 600 and max time to reconnect: 1800
2021/10/06 21:45:19 going daemon
Started ossec-agentd...
Started ossec-logcollector...
Started ossec-syscheckd...
Completed.Step 5: Test and Check Connection.
To check and confirm if OSSEC Agent connected and communicating with the OSSEC server simply check OSSEC logs on the Agent host.
$ tail -f /var/ossec/logs/ossec.log
2025/02/25 15:08:53 ossec-logcollector(1950): INFO: Analyzing file: '/var/log/dpkg.log'.
2025/02/25 15:08:53 ossec-logcollector(1950): INFO: Analyzing file: '/var/log/apache2/error.log'.
2025/02/25 15:08:53 ossec-logcollector(1950): INFO: Analyzing file: '/var/log/apache2/access.log'.
2025/02/25 15:08:53 ossec-logcollector: INFO: Monitoring output of command(360): df -P
2025/02/25 15:08:53 ossec-logcollector: INFO: Monitoring full output of command(360): netstat -tan |grep LISTEN |egrep -v '(127.0.0.1| ::1)' | sort
2025/02/25 15:08:53 ossec-logcollector: INFO: Monitoring full output of command(360): last -n 5
2025/02/25 15:08:53 ossec-logcollector: INFO: Started (pid: 25698).
2025/02/25 15:09:08 ossec-agentd(1210): ERROR: Queue '/queue/alerts/execq' not accessible: 'Queue not found'.
2025/02/25 15:09:08 ossec-agentd: INFO: Unable to connect to the active response queue (disabled).
2025/02/25 15:09:09 ossec-agentd(4102): INFO: Connected to server 192.168.1.186, port 1514.On the OSSEC server, check if the Agent is recognized and listed as Active.
$ sudo /var/ossec/bin/agent_control -lc
OSSEC HIDS agent_control. List of available agents:
ID: 000, Name: ubuntu-noble (server), IP: 127.0.0.1, Active/Local
ID: 001, Name: Ubuntu-01, IP: 192.168.1.162, ActiveCongratulations!!! OSSEC Agent is now installed successfully.
Step 6: Installing OSSEC Web Interface
For proper visualization and monitoring track of events, OSSEC has a suitable web interface that provides an awesome view of events.
Install Dependencies
Install Apache web-server.
sudo apt update -y
sudo apt install apache2 -yThen we’ll install PHP 7.4. Ubuntu 24.04 does not have PHP 7.4 in its default repositories, so you need to use Ondrej’s PPA:
sudo add-apt-repository ppa:ondrej/php -y
sudo apt updateNow, install PHP 7.4 and required extensions:
sudo apt install -y php7.4 php7.4-cli php7.4-common php7.4-mysql php7.4-xml php7.4-mbstring php7.4-curl php7.4-zip php7.4-gdCheck that PHP has been installed:
$ php -v
PHP 7.4.33 (cli) (built: Dec 24 2024 07:12:16) ( NTS )
Copyright (c) The PHP Group
Zend Engine v3.4.0, Copyright (c) Zend Technologies
with Zend OPcache v7.4.33, Copyright (c), by Zend TechnologiesInstall OSSEC Web UI
First, download the latest version of the OSSEC Web UI source from GitHub repository:
wget https://github.com/ossec/ossec-wui/archive/master.zipAfter downloading, extract the downloaded file with the following command:
unzip master.zipNext, move the extracted directory to the apache web root directory:
mv ossec-wui-master /var/www/html/ossecNext, install OSSEC Web UI with the following command:
cd /var/www/html/ossec
./setup.shFrom the below screen, you will be prompted to enter your username and password. These are the credentials you will need to login to your web interface. Choose web server user www-data.
Answer all the questions as shown below:
trap: SIGHUP: bad trap
Setting up ossec ui...
Username: admin
New password:
Re-type new password:
Adding password for user admin
Enter your web server user name (e.g. apache, www, nobody, www-data, ...)
www-data
You must restart your web server after this setup is done.
Setup completed successfully.Restart and enable the Apache web server.
sudo systemctl restart apache2
sudo systemctl enable apache2Check the status of apache2 service to confirm it is running:
$ systemctl status apache2
● apache2.service - The Apache HTTP Server
Loaded: loaded (/usr/lib/systemd/system/apache2.service; enabled; preset: enabled)
Active: active (running) since Tue 2025-02-25 15:17:13 EAT; 15s ago
Docs: https://httpd.apache.org/docs/2.4/
Main PID: 10442 (apache2)
Tasks: 55 (limit: 7015)
Memory: 5.5M (peak: 5.7M)
CPU: 30ms
CGroup: /system.slice/apache2.service
├─10442 /usr/sbin/apache2 -k start
├─10444 /usr/sbin/apache2 -k start
└─10445 /usr/sbin/apache2 -k start
Feb 25 15:17:13 ubuntu-noble systemd[1]: Starting apache2.service - The Apache HTTP Server...
Feb 25 15:17:13 ubuntu-noble apachectl[10441]: AH00558: apache2: Could not reliably determine the server's fully qualified domain name, using 127>
Feb 25 15:17:13 ubuntu-noble systemd[1]: Started apache2.service - The Apache HTTP Server.Now visit your http://SERVER_IP on your web browser to access the OSSEC interface.
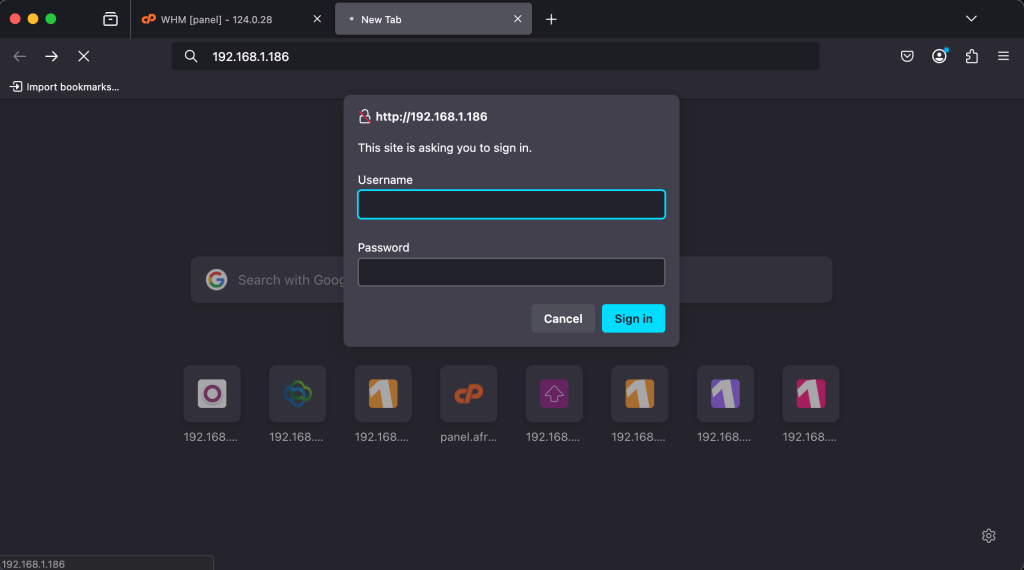
Use the username and password you set during the installation of the web interface to log in. And Voila, there’s your UI, you can view all the necessary logs.
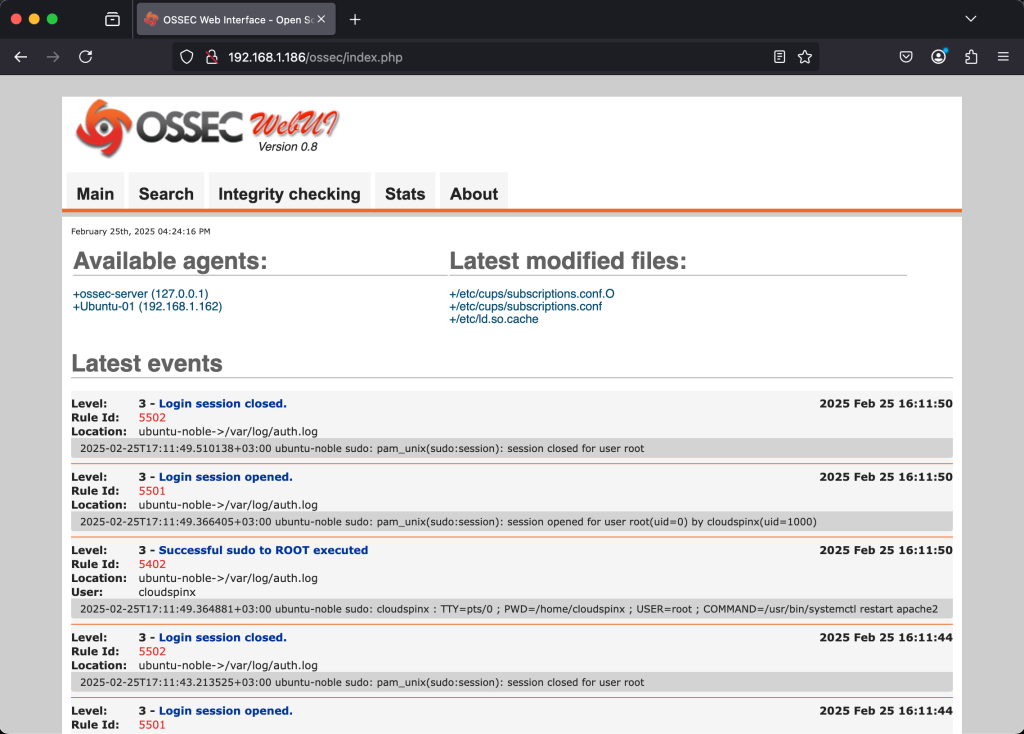
Conclusion
OSSEC agent keeps track of your server activity and update each and every event. Is a free software that you can acquire at zero cost with readily available community support. Thanks to everyone who is working towards providing best monitoring tools. Let OSSEC Agent keep an eye on your server/servers as you focus on productivity. BElow are interesting articles that might have missed.









