All-in-one hacking tool is an open-source tool that contains a bunch of tools integrated within a single framework. It is primarily designed to provide a set of tools for hackers to perform various tasks such as information gathering, vulnerability testing, and penetration-testing of websites and web applications. The facts that it is a complete framework with every tool necessary for hacking tasks, is very handy.
HackingTool is available in Windows, Linux and Android phones through the Termux, and android application that provides a Linux environment and terminal emulator for Android phones. It i written in Python and Bash.
Hacking Tools
Let’s have a look at some of the tools that HackingTool has to offer:
- Nmap – Nmap (“Network Mapper”) is an open source tool for network exploration and security auditing. It was designed to rapidly scan large networks, although it works fine against single hosts.
- Wifite – Wifite is an automated tool for wireless penetration testing that makes use of the Reacver and WPS command-line tools, as well as the utilities connected to Aircrack-ng.
- sqlmap – sqlmap is an open source penetration testing tool that makes it easy to find and take advantage in exploiting vulnerable flaws in database servers through SQL injection.
- Evilginx – Using session cookies and phishing login credentials, Evilginx is a man-in-the-middle attack framework that makes it possible to go around 2-factor authentication security.
- Dirb – DIRB is a Web Content Scanner. It looks for existing (and/or hidden) Web Objects. It basically works by launching a dictionary based attack against a web server and analizing the response.
- The FatRat – TheFatRat is an exploiting tool which compiles a malware with famous payload, and then the compiled maware can be executed on Linux , Windows , Mac and Android.
- Commix – Commix, short for ([comm]and and [i]njection e[x]ploiter), is an open source penetration testing tool, that automates the detection and exploitation of command injection vulnerabilities.
- Brutal – Brutal is a penetration-testing tool extremely useful for executing scripts on a target machine without the need for human-to-keyboard interaction ( HID -ATTACK ).
- pyshell – pyshell is a simple remote access trojan that makes it easy to gain access to a target machine.
Complete Setup of Hackingtool For Hackers
To install Hacking tool, follow the following steps:
Step 1: Download Hackingtool
To download hacking tool, clone the GitHub repository by running the command below:
git clone https://github.com/Z4nzu/hackingtool.gitStep 2: Give permissions to Hackingtool
You need to give read, write and executable permissions to the hacking tool files and directories. Run the following command:
sudo chmod -R 755 hackingtool Step 3: Change to Hackingool directory
Now, change to hackingtool directory, where you’ll run the install script:
cd hackingtoolStep 4: Install dependencies
Now that you are in the tool’s directory, use the following command to install dependencies of the tool:
sudo pip3 install -r requirements.txtSample Output:
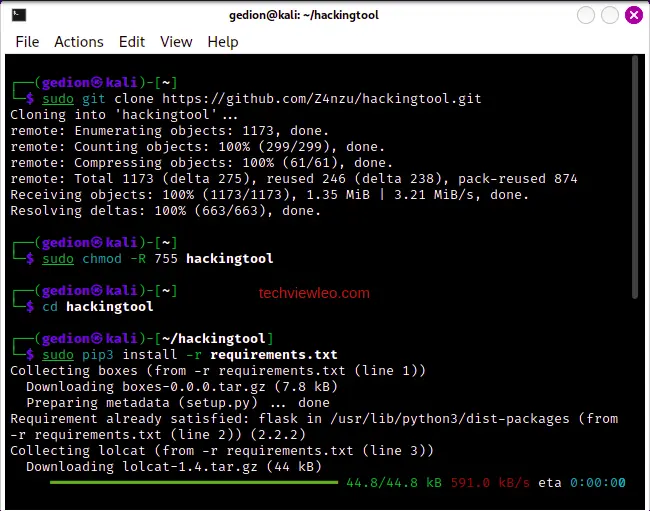
Step 5: Running and Using hackingtool
Run the install script to install Hackingtool:
sudo bash install.shSample Output:
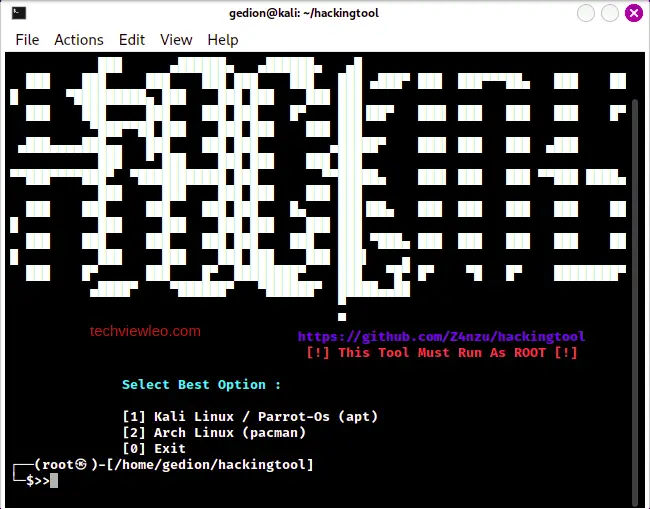
Choose option 1 to install hackingtool on your Kali Linux or Parrot-OS and option 2 for Arch Linux:
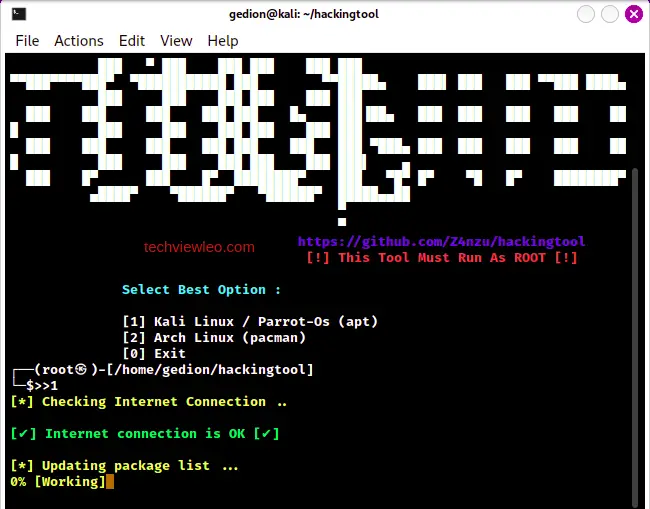
When prompted to select the character set for the console font, choose whichever you prefer and proceed:
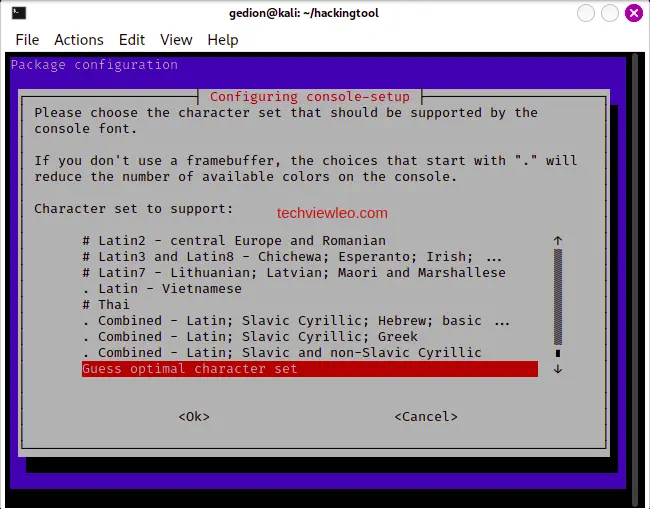
Allow hackingtool to install and complete setup. When the process is complete, hackingtool is ready:
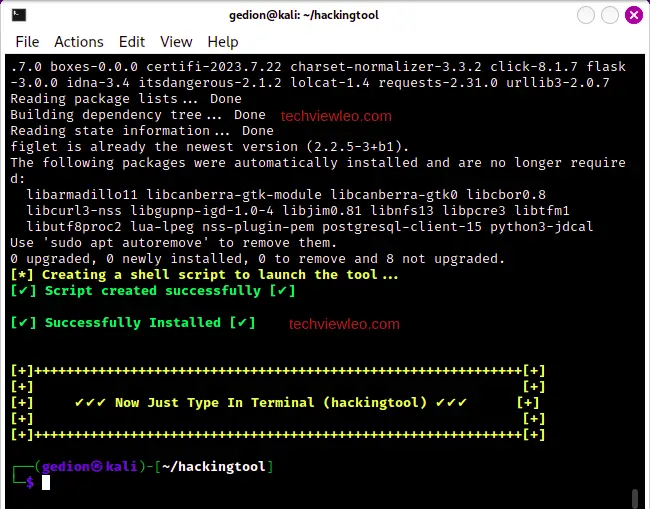
Usage
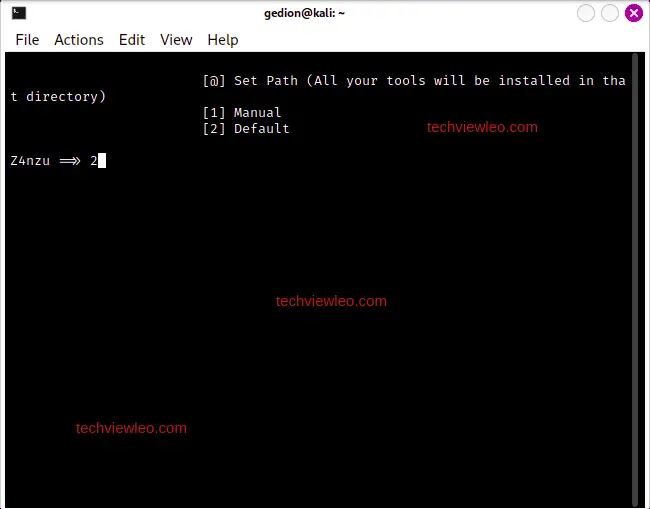
Execute the following command to run hackingtool and install the tools in directory:
sudo hackingtoolThen select option 2 and hit enter to install the tools in the default directory, which is /home/hackingtool:
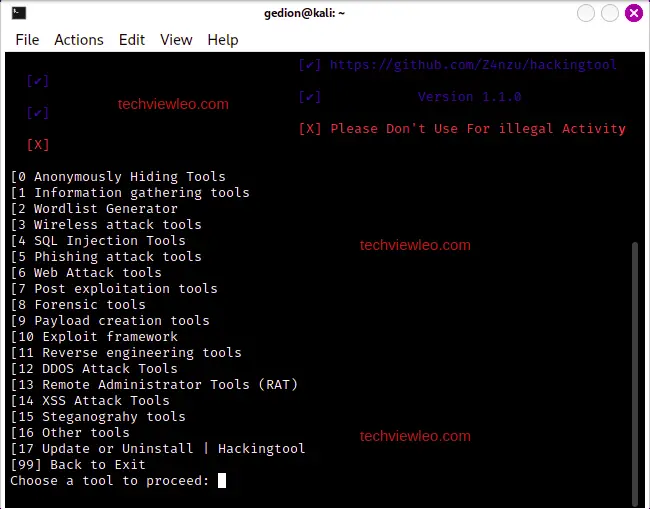
This displays the tool menu for all the hacking tools:
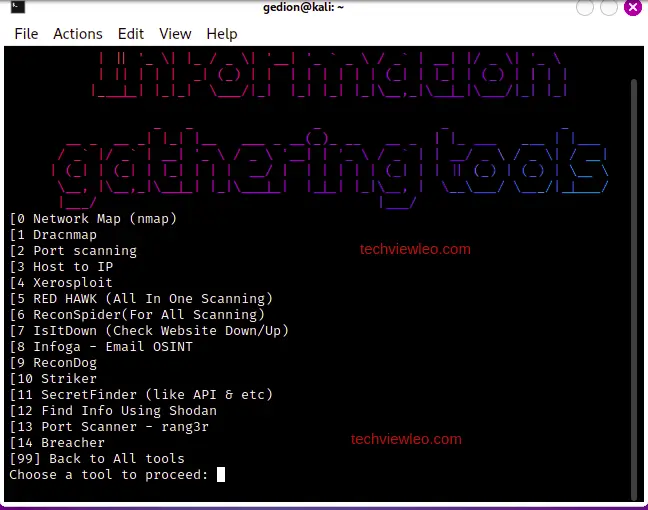
Select any category of tools and proceed:
And select one of the tools from the category you selected. Now, you might need to install a tool before using it, so select the install option:
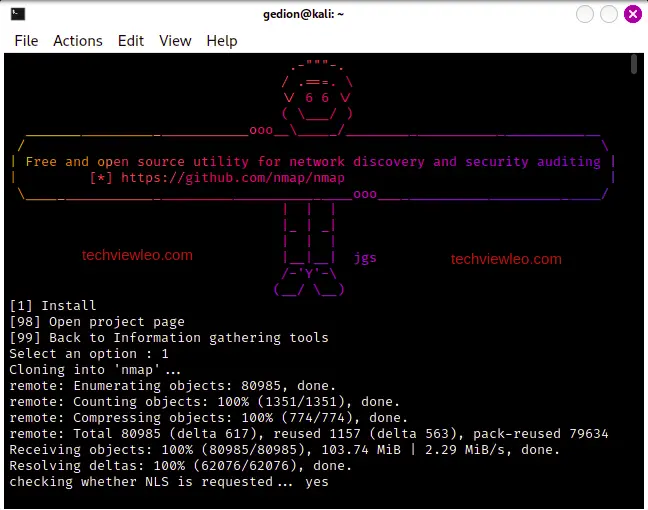
But for some tools, you can just run them since they have already been installed:
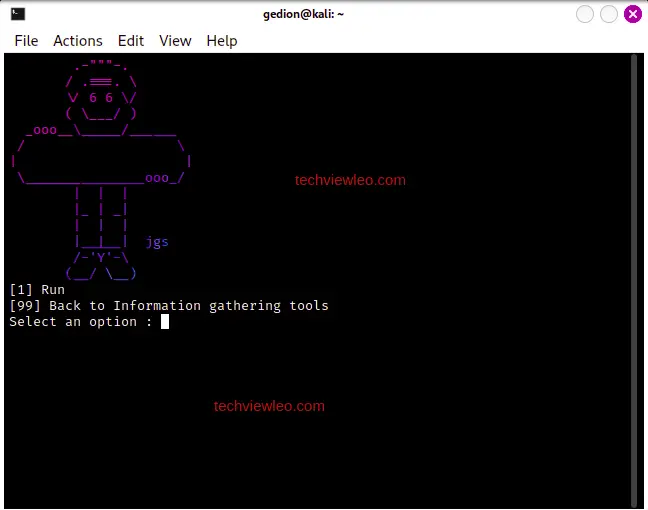
For such a tool, select the run option to use the tool:
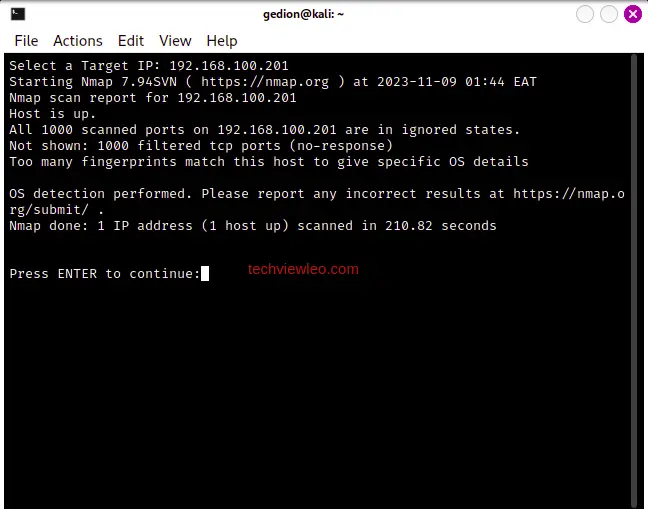
You can access any tool you’d like, just install it and then go ahead and run the tool. Have fun!
Conclusion
Generally, HackingTool comes in very handy when you want to access all your tools in one place. It provides a bunch of hacking tools and categorize all the tools according to their fields of expertise. Each tool can be installed and run in the hackingtool directory. The good thing about hackingtool is that it introduces you to new tools in each category and provides a bunch of options for that specific field.








