Websploit is an open-source framework for testing websites and networks. It is a simple to use written in Python. It makes use of modules to perform activities such as directory scanning, wireless attacks and man-in-the-middle. In this guide, we are looking at how to install and use Websploit on Linux.
🔑 Unlock the complete Ubuntu Desktop learning journey by purchasing our best selling ebook: The Ultimate Ubuntu Desktop Handbook.
Install Websploit on Ubuntu | Debian Linux
Run the below command to install websploit framework on Ubuntu and Debian systems:
sudo apt update
sudo apt install websploitOnce installed, we should be able to run the tool. We simply run the command ‘websploit’ on the terminal to launch it:
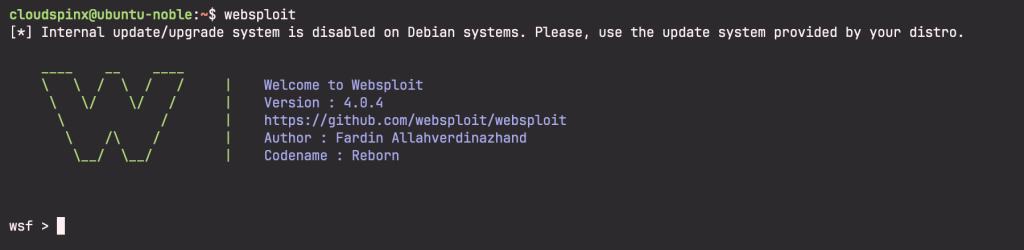
You will notice that Websploit works in the same way as Metasploit. Both use modules, similar commands and have a welcome banner. If you are familiar with Metasploit, you should not find any difficulty using websploit.
To show commands to use with Websploit, simply type ‘help’ at the interactive prompt.
wsf > help
Commands
========
about exit help show update useAnother good thing about Websploit just like metasploit is that you don’t have to exit websploit interactive mode in order to run operating system commands. What you have to do is to type the commands as usual from the websploit interactive shell. Example, show your system network settings.
wsf > ip address
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host noprefixroute
valid_lft forever preferred_lft forever
2: enp1s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 52:54:00:27:94:dd brd ff:ff:ff:ff:ff:ff
inet 192.168.1.182/24 metric 100 brd 192.168.1.255 scope global dynamic enp1s0
valid_lft 4591sec preferred_lft 4591sec
inet6 fe80::5054:ff:fe27:94dd/64 scope link
valid_lft forever preferred_lft foreverTo check available modules, run the command below:
wsf > show modules
Modules Description
-------------------- --------------------------
arp_spoof ARP Cache poisoning
http_sniffer Sniff HTTP traffic
scan_network Scan IP range for new devices
scan_wifi Scan Wireless devices
wifi_deauth Force device to disconnect from WIFI - De-authentication attack
wifi_fap Start Fake Access point (AP)
wifi_fap_spam Spamming Fake access points To use a module use the command as ‘use’ together with the module you wish to use. Example as below:
wsf > use scan_network
wsf > scan_network > You can then show the options that are available within the module as below:
wsf > scan_network > options
Option Value
---------------- ----------------
ip 192.168.1.1/24 You can set now set your target using the IP you want to reach:
wsf > scan_network > set target 192.168.1.5
target 192.168.1.5Run the module using ‘execute’ command:
wsf > scan_network > executeYou have successfully installed Websploit Framework on Ubuntu | Debian. I hope you enjoy using it to perform systems scans. Refer to Websploit documentation for more insights.
More guides from us: