Grub, an acronym of Grand Unified Bootloader is the most preferred boot loader on Linux systems although there are others such as GRUB2 and LILO. Grub is a bootloader package and implementation of the Free Software Foundation’s Multiboot Specification licensed under the GNU project. It is preferred because it allows the user to boot between multiple operating systems installed on the computer or also choose the kernel configuration for the system.
Why set the GRUB password?
Setting a GRUB password on Linux is very important. I am pretty sure that you know that once a person gets access to the Linux system it is so easy to reset the root password by booting into the single-user mode. This is the main reason why you should secure your GRUB. This restricts one from editing menu entries, they have to provide the GRUB password first to proceed.
This guide takes a deep dive into demonstrating how to protect GRUB with password on Rocky Linux 9 | AlmaLinux 9.
Step 1 – Set the GRUB password
There are two methods you can use to set the GRUB password on Rocky Linux 9 | AlmaLinux 9.
The Simple Method
On Rocky Linux/Alma Linux, the GRUB loader is shipped with a simple command to set a password for the boot menu. This command will set a password for the default root user.
$ sudo grub2-setpassword
Enter password:
Confirm password:That is it!
In case you want to remove the set GRUB password using this method, simply delete the files below.
##For BIOS-Based
sudo rm -f /boot/grub2/user.cfg
##FOR UEFI-Based
#Rocky Linux
sudo rm -f /boot/efi/EFI/rocky/user.cfg
#AlmaLinux
sudo rm -f /boot/efi/EFI/almalinux/user.cfgIt is always safe to delete the file in both locations.
The Advanced Method
This method works best for those who want to create multiple login credentials for the GRUB menu.
Generate a password hash for your multiple users as below.
$ sudo grub2-mkpasswd-pbkdf2
Enter password:
Reenter password:
PBKDF2 hash of your password is grub.pbkdf2.sha512.10000.B5A76A42F34981D880C04B7687F8CAADF7D19ECA70F75B9D0C8E815D4CBF9BD42A341D5A8ED1222ADCF281F200EB5A365B5F616B5029153A485BCA1CB2F06875.8E3A9FEB15221D4CF3B3A47B6DB7B72F1287F1149D78CB2B8577A10327A3CEE9EEAE74ABFFA63C68C5933A9FD34298ECC8AB8B38A90EE4193BAC56ECF0224E9E
$ sudo grub2-mkpasswd-pbkdf2
Enter password:
Reenter password:
PBKDF2 hash of your password is grub.pbkdf2.sha512.10000.7D6D1913A2D066AB00AE68B718C777504704A17E726DA7923794073D50D657549545A7D0934DA2D02B946678DA17D44856D43F9F4A65E30CC2FE9D0DB880ABDC.BA69F7AE826FD5D11B00E7FBB4E42EDCC63C583A7077E457F036B2CE2BB25A48232FB2E74622A18B8F5D2F3E9008369D3689EE2C1CCC150EB3EC1DE3923755DAAs seen from the output, we have the two PBKDF2 hash passwords generated. Two passwords have been generated because we want to have multiple login credentials. Now proceed and add them to the /etc/grub.d/00_header.
it is always recommended that you take a backup of these files before editing them.
sudo cp /etc/grub.d/00_header /etc/grub.d/00_header.bakNow edit the files.
sudo vi /etc/grub.d/00_headerAt the end of the file, add the generated hash passwords as below.
cat << EOF
set superusers="root,thor"
password_pbkdf2 root grub.pbkdf2.sha512.10000.B5A76A42F34981D880C04B7687F8CAADF7D19ECA70F75B9D0C8E815D4CBF9BD42A341D5A8ED1222ADCF281F200EB5A365B5F616B5029153A485BCA1CB2F06875.8E3A9FEB15221D4CF3B3A47B6DB7B72F1287F1149D78CB2B8577A10327A3CEE9EEAE74ABFFA63C68C5933A9FD34298ECC8AB8B38A90EE4193BAC56ECF0224E9E
password_pbkdf2 thor grub.pbkdf2.sha512.10000.7D6D1913A2D066AB00AE68B718C777504704A17E726DA7923794073D50D657549545A7D0934DA2D02B946678DA17D44856D43F9F4A65E30CC2FE9D0DB880ABDC.BA69F7AE826FD5D11B00E7FBB4E42EDCC63C583A7077E457F036B2CE2BB25A48232FB2E74622A18B8F5D2F3E9008369D3689EE2C1CCC150EB3EC1DE3923755DAFor the changes made to apply, update GRUB.
$ sudo grub2-mkconfig > /boot/grub2/grub.cfg
Generating grub configuration file ...
doneIn case you want to remove the GRUB password, just edit the file and remove the added lines. Alternatively, revert to the backup file taken.
Step 2 – Verify the set GRUB Password
With whichever method you used to set the GRUB password, reboot your system.
sudo reboot -iProceed to the GRUB menu. Here, we want to see if we can edit the GRUB menu entries.
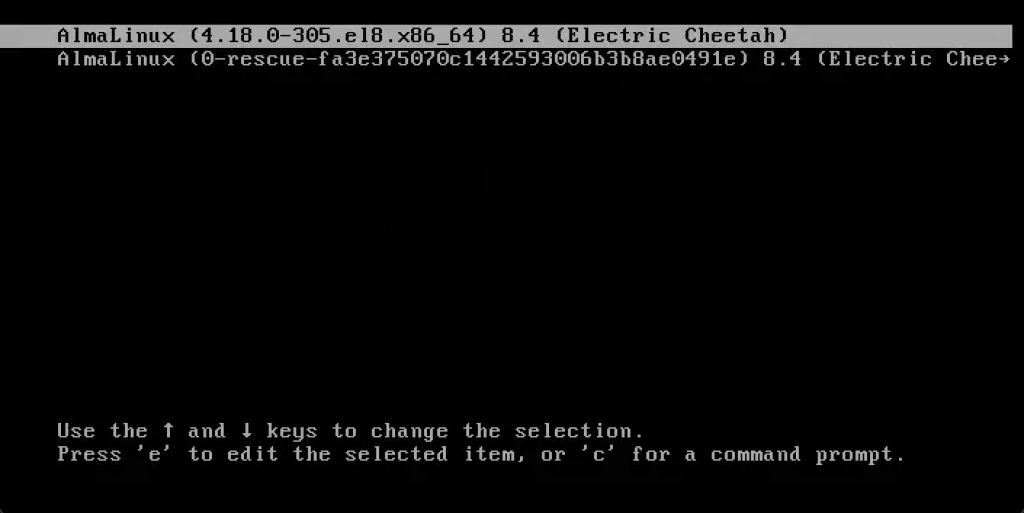
Press e, you will be asked to provide the username and password set.
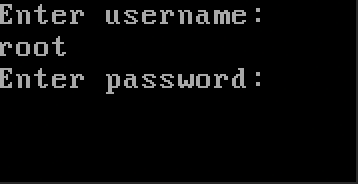
With the correct details provided, you will be able to edit the GRUB as below.
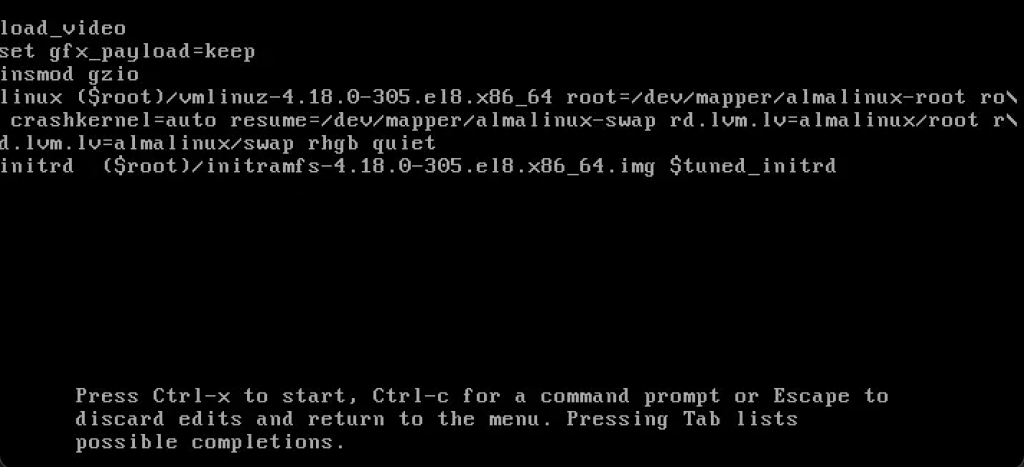
The output confirms that we have successfully protected GRUB with password on Rocky Linux 9 | AlmaLinux 9. Now anyone who tries to edit the GRUB entries should provide the password. I hope this was helpful.
See more:









