Welcome to this guide on how to use SSH & SSH Keys on Debian 12/11/10. SSH stands for secure shell, this is a cryptographic protocol used to administer and establish communication between servers. It supports various authentication mechanisms with the common ones being password and public-key-based authentication mechanisms.
Authentication using a Public key is more secure as compared to password authentication since it is based on the use of digital signatures.
OpenSSH(OpenBSD Secure Shell) is a project developed as part of the OpenBSD project by Theo de Raadt. It contains a set of all applications required to provide an encrypted communication session on a computer using SSH.
Let’s dive in!
1) Install OpenSSH Server on Debian 12/11/10
this is the application that provides the SSH services on Debian 12/11/10 as explained above. Install it using the below command.
sudo apt update
sudo apt install openssh-serverOnce the installation is complete, start the SSH service.
sudo systemctl start sshEnable the SSH service to run automatically on boot.
sudo systemctl enable sshVerify the service is running correctly.
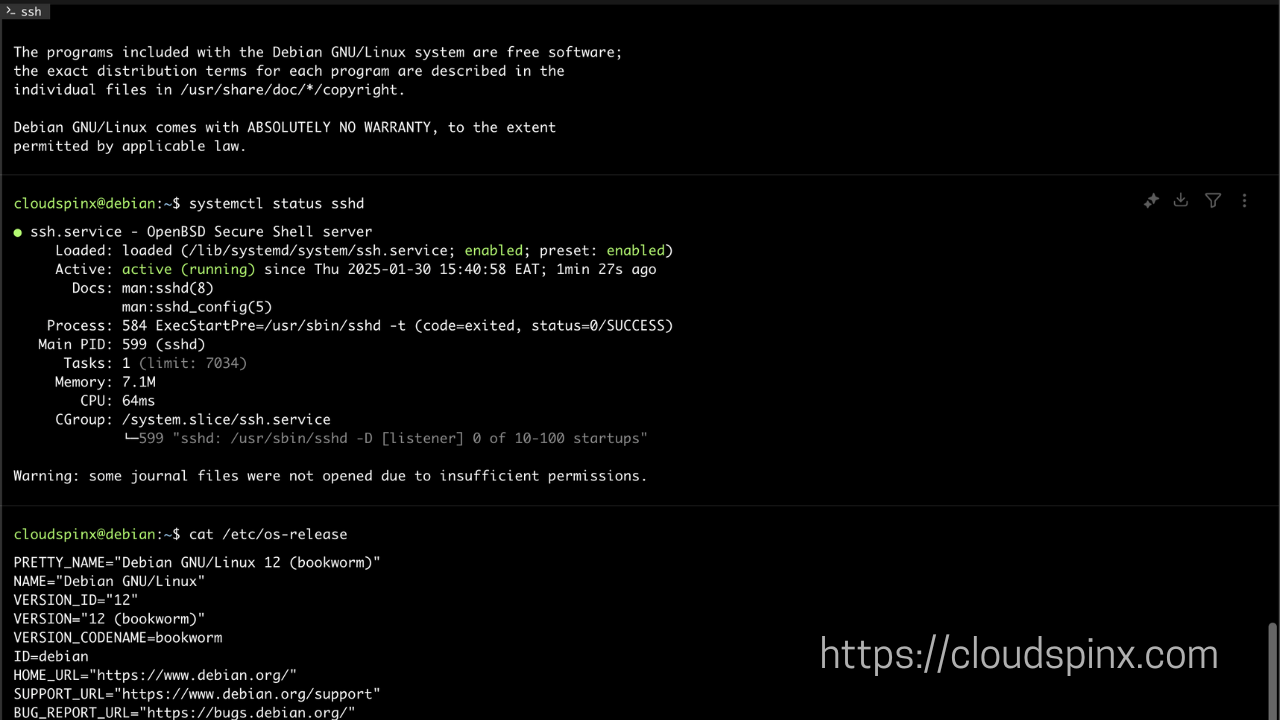
$ systemctl status ssh
● ssh.service - OpenBSD Secure Shell server
Loaded: loaded (/lib/systemd/system/ssh.service; enabled; vendor preset: e>
Active: active (running) since Thu 2025-01-30 10:22:54 EAT; 1s ago
Docs: man:sshd(8)
man:sshd_config(5)
Process: 86999 ExecStartPre=/usr/sbin/sshd -t (code=exited, status=0/SUCCES>
Main PID: 87017 (sshd)
Tasks: 1 (limit: 14183)
Memory: 1.4M
CGroup: /system.slice/ssh.service
└─87017 sshd: /usr/sbin/sshd -D [listener] 0 of 10-100 startups
Jan 30 10:22:54 lab systemd[1]: Starting OpenBSD Secure Shell server...
Jan 30 10:22:54 lab sshd[87017]: Server listening on 0.0.0.0 port 22.2) Create the RSA Key Pair on Debian 12/11/10
Now we need to generate the RSA key pair, this pair is comprised of the Private and Public keys. It is generated using the command:
$ ssh-keygenNormally, the command above generates a 3072-bit RSA key pair, this is secure enough but you might also use the -b 4096 to create a more secure 4096-bit key.
Proceed as below.
Generating public/private rsa key pair.
Enter file in which to save the key (/home/thor/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
nter same passphrase again:
Your identification has been saved in /home/thor/.ssh/id_rsa
Your public key has been saved in /home/thor/.ssh/id_rsa.pub
The key fingerprint is:
SHA256:KI/YmH32E6OXZJJv+vvU3ppVR6Y3e4jc2hD7g thor@debian
The key's randomart image is:
+---[RSA 3072]----+
| |
| |
| .|
| . *.|
| . ..S ==O|
| * +o = ..+XX|
| + + +* + . o+o*|
| o..*. .o o. |
| .=+o.E++.. |
+----[SHA256]-----+Using a passphrase will add an additional security layer that prevents your authorized keys from being used by unknown users. You have now generated a public key that you can use to log in to another server using key-based authentication.
3) Copy the Public Key to a Remote Server(Debian)
Now we want to copy the generated public key to another server. In this case, the other server is a Debian server as well, but you still can use a server of your choice. Copying this public key allows the two servers to communicate using the key added.
There are multiple ways to copy the SSH keys.
3.1. Copy the Public Key Using ssh-copy-id Command
The tool ssh-copy-id is available by default in many operating systems. This method works if you already have Password-based communication between the two servers already enabled.
This tool is used by specifying the user account and the IP Address of the remote host you want to connect to.
ssh-copy-id username@remote_hostSample output:
$ ssh-copy-id [email protected]
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/home/thor/.ssh/id_rsa.pub"
The authenticity of host '192.168.205.14 (192.168.205.14)' can't be established.
ECDSA key fingerprint is SHA256:ILxwNPGGeJNCJAFKGr3WN7xTlVEHmzBnu1E9J88.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
[email protected]'s password: Enter Password Here
Number of key(s) added: 1
Now try logging into the machine, with: "ssh '[email protected]'"
and check to make sure that only the key(s) you wanted were added.From the output, we have to authenticate with a password first, so that the keys can be copied to the remote host.
3.2. Copy the Public Key Using SSH
Another method you can use to copy the SSH key is by using SSH. This also works when you have password-based SSH access to the remote host. SSH allows one to upload files, documents to another host.
First, you have to ensure the ~/.ssh directory exists on the remote host with the correct permissions.
We will then use the command with the syntax below to avoid destroying previously added keys.
cat ~/.ssh/id_rsa.pub | ssh username@remote_host "mkdir -p ~/.ssh && touch ~/.ssh/authorized_keys && chmod -R $USER ~/.ssh && cat >> ~/.ssh/authorized_keys"Sample Output:
The authenticity of host '192.168.205.14 (192.168.205.14)' can't be established.
ECDSA key fingerprint is SHA256:ILxwNPGGeJNCJAF64K5KGr3WN7xEHmzBnu1E9J88.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
[email protected]'s password: Enter Password HereEnter “Yes” for the server to recognize the remote host. Also, authenticate with a password and the keys will be copied.
3.3. Copy the Public Key Manually.
This method now is for those who do not have password-based SSH access. This method involves the below steps.
First, view the public key using the cat command as below.
$ cat ~/.ssh/id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDQ0I4DyPXXvxbli9UDmm3gR8l5hZTo8shd59tYBwdAofgkLKxdYfwEhyXv7F5aRK3E59ORx55bPEpMusgFELlXkaZVsoK5Gts1nykYblc8YT7nj9fYXeHcwrOSgp6zOLowhXC4GT1vHF5vGQQO6gd5Rp/3R2G3g/bEh6/lkNBMNwNGXWzpWXoHx2Jpftlh1VQXJgUtzsTs21wEr9K/XYxjCMUZgHdHAKNxF3itWo0Gd/sZ9AVH60SBh2J38ErxxPyzu5ir5n3CBW3k.....xjae3XE6sQLXzF1iFLTkmZsDC3JREsyrbSG26+P7htfHklNkr4UKJPGWaI+2POOvmWk241XyY4UJ5/yCBllpVEoM/UPHNtn/CV6fcXmQ/jsfXxc0TcBsn5exfDePTK9PZMCiP6VgeBZCQhS+ZS+MoXEfaVHDW9aXNxiwlb3n5T8= thor@debianNow go to the remote server using the available method and ensure that the ~/.ssh directory exists. If not, you can create it using the command.
mkdir -p ~/.sshIn the directory, create the authorized keys file.
touch ~/.ssh/authorized_keysAssing the required permissions to the created directory.
chown -R user:user ~/.sshSubstitute user:user with the appropriate system username.
Edit the file and add the public key.
vim ~/.ssh/authorized_keysNow paste the public key generated on the source host string to the ~/.ssh/authorized_keys remote host starting with ssh-rsa AAAA..
4) Authenticate to remote systems using SSH Keys
Now that the public key has been copied to the remote host, let’s connect to it using SSH-based authentication.
The syntax used is as below.
ssh username@remote_hostSample Output:
$ ssh [email protected]
Linux debian 5.10.0-9-amd64 #1 SMP Debian 5.10.70-1 (2021-09-30) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Nov 20 02:34:38 2021 from 192.168.205.1
thor@debian:~$ From the output, our SSH-key-based authentication is working correctly. We haven’t input a password to be logged in.
5) Disable Password Authentication on the Remote Server.
Now to enhance security, you need to disable password login on the remote host and allow it to use SSH-key-based authentication only. After confirming that the SSH-key-based authentication is working perfectly, procced and disable password login on the remote host as below.
Edit the config file below.
sudo vim /etc/ssh/sshd_configIn the file, set PasswordAuthentication to no as shown.
# To disable tunneled clear text passwords, change to no here!
PasswordAuthentication no
#PermitEmptyPasswords noSave the file and restart ssh for the changes to be applied.
sudo systemctl restart sshNow you can test one more last time if the SSH-key-based authentication is working.
ssh username@remote_host6) Copy files over SSH Using SCP
With SSH, one can transfer files between two hosts. SCP is used to securely transfer files and directories between two hosts without starting the FTP session, it uses SSH to transfer data. After exchanging keys as above, this process becomes as easy as robbing a child’s bank.
The syntax used is as below.
scp [options] username@source_host:directory1/filename1 username@remote_host:directory2/filename2In the command, replace the hosts and usernames appropriately. Remember directory1/filename1 is the file to be copied and directory2/filename2 is where you want to paste the copied file.
Copy a Local File to a Remote System
For example, to copy a file named thor.txt from my local host to a remote host to the HOME directory, I will use the command as below.
$ scp ~/thor.txt [email protected]:~/
thor.txt 100% 13 19.3KB/s 00:00 The file will be copied to the remote host 192.168.205.4 in the directory ~/.
Copy a Remote File to a Local System
Now to copy a file from the remote host to a local system, use the syntax below.
scp username@remote_host:/remote/file.txt /local/directory7) Using ssh-agent and ssh-add commands
In Linux systems. the ssh-agent is used to handle passwords for the SSH private keys. Using the ssh-add command, the user adds the password of their Private key to the list maintained by the ssh-agent. With the password added, the user will not be prompted to enter their password when using SSH or SCP to connect using their Public key.
eval `ssh-agent`Now add the key to the ssh-agent.
ssh-addProvide the private key password.
Enter passphrase for /home/thor/.ssh/id_rsa: Enter Password
Identity added: /home/thor/.ssh/id_rsa (thor@debian)
Identity added: /home/thor/.ssh/id_ed25519 (My key for Linux server # 42)8) Configure SSH to run on a non-standard port.
Normally SSH runs on port 22, however, it can be configured to run on any preferred port.
Edit the file below on the server-side.
sudo vim /etc/ssh/sshd_configIn the file, find, uncomment and edit the port to your preferred one as below.
Port 2543Save the file and restart SSH.
sudo systemctl restart sshNow any connection using port 22 will drop and you will be required to connect using the new port.
ssh -p 2543 username@remote_host9) Foward X session over SSH.
The X session tunneling allows one to run the graphics applications remotely. This can be made default to all connections by editing the conf file as below. Remember, that X11 forwarding needs to be enabled on both sides.
sudo vim /etc/ssh/sshd_configIn the file, edit the line to match the below content.
X11Forwarding yes
X11DisplayOffset 10Restart SSH.
sudo systemctl restart sshEnsure the .xauthority directory exists on the remote server.
$ xauth
xauth: file /home/thor/.Xauthority does not exist
Using authority file /home/thor/.Xauthority
xauth>Now connect to the X session over SSH using:
ssh -X username@remote_hostConclusion
Now you are set to go! That was enough learning, I hope you enjoyed this guide on how to use SSH & SSH Keys on Debian 12/11/10. In case you had troubles with this setup, let us know in the comments below.
See more on this page: